In this time where everybody is attempting to ensure their information and protection, we hear a considerable measure about the TOR network. Some sing acclaim while others think of it as an apparatus for crooks. In this article, we give you the working standards of TOR by portraying likewise its preferences and drawbacks.
WHAT IS THE TOR NETWORK?

TOR remains for The Onion Router, and it’s a non-profit association that spotlights on securing the protection and obscurity of Internet clients on the web. The TOR network is intended to keep governments or privately owned businesses from keeping an eye on you.
In light of this perception, the TOR network works by going to your organization through various transfer focuses that are overseen by a large number of volunteers the world over. In this manner, it is difficult to assault the TOR network frontally due to its decentralized nature.
The TOR network depends on two major standards, specifically, the product that enables you to associate with the network and the volunteers who offer servers around the globe.
WHO CREATED THE TOR NETWORK?
The TOR innovation was composed by the US Navy and the Department of Defense financed the venture to more than 60%. Another financing originates from organizations that ensure protection, for example, the EFF, writers’ affiliations and lobbyist gatherings. The TOR network truly took off in 2002 when designers wanted to offer a namelessness arrangement in a time where Internet clients gave their data for nothing out of pocket without their assent.
If we offer you a record for nothing, at that point you are the item! Today, TOR is a totally autonomous association and the venture is open source with the goal that everybody can see the code and right it is fundamental.
TOR’s innovation depends on the alleged Onion Routing that was created by Michael G. Reed, Paul F. Syverson, and David M. Goldschlag in the 1990s and is claimed by the US Navy. Note that we are discussing innovation and not the TOR venture.
The last was created by Syverson, Roger Dingledine, and Nick Mathewson and it was formally named as the TOR venture. It was presented and propelled on September 20, 2012. In 2004, the US Navy discharged the TOR code, which is as of now being produced by the group, for nothing.
WHAT IS ONION ROUTING?

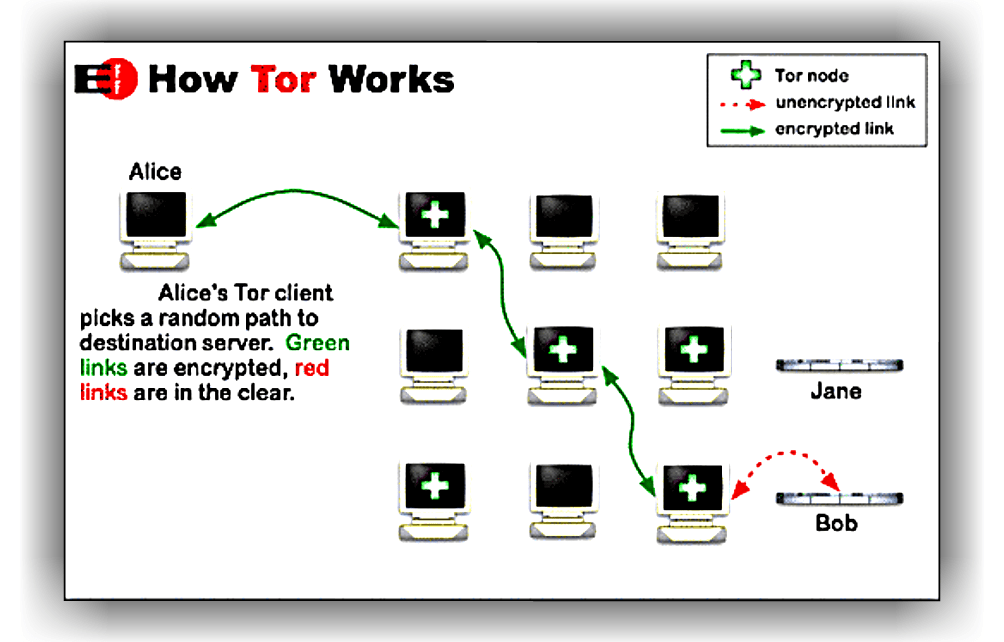
Onion Routing is an anonymous correspondence strategy over a network. The messages are encoded persistently and they are sent by means of network hubs called Onions routers. You will regularly observe the onion image on the TOR network, however, this has nothing to do with the vegetable. This onion alludes to the distinctive layers of encryption that ensure the messages. At the point when a data is sent to TOR, it is scrambled and re-encoded a few times consecutively on anonymous transfers.
Each hand-off will include an encryption level that will change when it achieves the following transfer. The fundamental favorable position of this encryption is that the steering is absolutely imperceptible.
Nonetheless, the TOR network does not secure interchanges when they leave the network. Likewise, TOR offers decent obscurity on the off chance that you utilize it with other encryption apparatuses. Furthermore, the principle disservice of TOR is its gradualness, on the grounds that the data must go through various transfers previously touching base at their goal.
WHAT ARE THE ONION ROUTERS?
The computerized transfers are called routers or hubs. They get the movement from the TOR network and exchange it. TOR’s authentic site offers an itemized record on how it functions. There are 3 sorts of transfers that you can dispatch on the advanced network which are the middle hand-off, the yield hand-off, and the extension.
For most extreme security, all TOR movement goes through these 3 transfers before achieving its goal. The initial 2 are go-between transfers that get the movement and exchange it to another hand-off.
Moderate transfers enhance the speed and heartiness of the TOR network, staying away from the middle person hand-off proprietor from being recognized as the wellspring of the activity.
The moderate hand-off will caution clients that it is accessible for them to associate with and increment their association speed.
Therefore, if a man utilizes the TOR network for pernicious exercises, the IP address of the middle person hand-off won’t be considered as the wellspring of the activity. In light of what has been said that you don’t run any hazard on the off chance that you need to propose a middle person TOR transfer from your PC.
Leave transfer is another story. The transfer passes the activity before it achieves its goal. The yield hand-off will caution the whole TOR network and all clients can utilize it. Since the TOR activity goes out through this transfer, the IP address of this hand-off is viewed as the wellspring of the movement.
Accordingly, noxious utilize by means of this yield hand-off can accuse the proprietor of this hand-off. Discharge transfer proprietors must comprehend that they will be the objective of copyright affiliations and governments. In the event that you would prefer not to have this sort of issue, at that point the utilization of the halfway transfer is suggested for greater security.
At long last, spans are computerized transfers that are not noticeable on the network. The scaffold is basic in the nations that piece the TOR transfers that are open. When all is said in done, you can dispatch an advanced scaffold on your PC with no issue.
IS THE TOR NETWORK RIGHT FOR YOU?
As you read this article, you most likely feel that TOR exceeds expectations in the security of protection. What’s more, we can state that it is a decent apparatus. Be that as it may, at the base, TOR was intended to ensure flexibility of articulation and to evade control in nations, for example, Saudi Arabia or China. On the off chance that you are a blogger in these classes of nations, at that point, the TOR network enables you to skirt the obstructing of neighborhood ISPs and access all data accessible on the web. It additionally enables writers to impart safely to keep the government from ceasing them.
TOR’S HIDDEN SERVICES OR.ONION SITES
The TOR network does not just empower secure correspondence, it likewise enables the substance to be facilitated in servers that exclusive acknowledge computerized associations. Everybody knows the locales in .com, .organization, .data, and so on.In any case, the TOR network offers locales that end with the .onion expansion. These locales are supposed shrouded administrations and they offer substance that isn’t noticeable on the standard web. For instance, the Silk Road stage utilized these .onion destinations to offer weapons, drugs, and so on.
Also, these concealed administrations don’t utilize exit transfers (since they are inside TORs) thus it is exceptionally hard to recognize visitors to these destinations. In any case, it isn’t unthinkable, on the grounds that it is sufficient that the TOR server is severely designed with the goal that we can recognize the visitors.
DO YOU HAVE TO USE TOR?
TOR is a decent device to ensure your protection and secrecy, yet it is a long way from consummate. The principal thing is that governments begin to painstakingly monitor exit transfers and on the off chance that they distinguish you, at that point, you will end up being a prime target.
What’s more, the fundamental downside of TOR is the gradualness of the association, which is now and again cataclysmic. Now and again, the association is slow to the point that it ends up noticeably unusable.
It has been said that the TOR network is secure, yet this isn’t the situation for your program. On the off chance that you don’t play it safe, at that point, an office like the NSA can capture the information in your program and the utilization of the TOR network won’t be utilized anymore since they will have the capacity to track the program.
FINAL VERDICT
If users of the TOR network are often the target of government agencies, you will never have trouble with the VPN. Indeed, you can change IP address as many times as you want and you can also choose servers that are distributed worldwide. The TOR network allows you to have some anonymity, but the VPN allows you to use the web without any restrictions and is thought to be the best definition of freedom of expression.