Once you learn top ethical hacking terminologies, it’s time to learn how to protect your online identity. These days it is one of the biggest challenges to stay anonymous while browsing the web. In this article, I will mention ways to stay anonymous online.
I have discussed this topic in detail in the past. But in this article, I will also discuss popular methods to hide identity on the Internet with their pros and cons.
Basically, there are three methods to hide identity on the Internet. Hide behind the VPN, Proxy, and use the Tor network.
VPN
What’s VPN?
VPN stands for Virtual Private Network. VPN provides an encrypted tunnel which is great for surfing the internet securely over public wifi. Using VPN makes it look like the request is coming from a different location rather than the users’ real location. VPNs work on the operating system level, which means web browser traffic and any traffic generated from the system’s applications are routed through the VPN.

One of the benefits of using VPNs is that VPNs are faster than most proxies and tor network. But VPNs can not be trusted for journalism, activism, or any other serious job. Usually, for a good VPN, users have to pay. Free VPNs are slow, plus they most likely log their users’ activities.
Paying itself is leaving a trace for others to follow you. Secondly, several popular VPN providers claim not to log users’ activities, but incidents have shown it’s difficult to trust them. Last year, several VPN providers leaked a huge database that included sensitive data such as users’ email, home addresses, IP addresses, plain text passwords, and even the logs of users’ activities. All these VPN providers included in the leak had claimed not to log users’ activities, but it turned out to be false.
So when it comes to VPN providers, they can not be trusted for some serious jobs unless you build your own VPN network or find the correct one in the market.
Pros of VPN
- Easy to use
- Encrypt users traffic
- Best for accessing blocked websites faster
- Works on the Operating system level
Const of VPN
- Difficult to find the correct one (Many will store users activity logs)
- Have to pay to route traffic from specific countries
Proxy
What is Proxy?
Proxy works similarly. Proxy routes traffic from a remote computer so that the destination server does not get the user’s real IP address. So this hides the user from the destination server, say google.com. Unlike VPN, Proxy does not work at the operating system level. The proxy user can only route traffic generated from a specific application, and other applications will work normally.
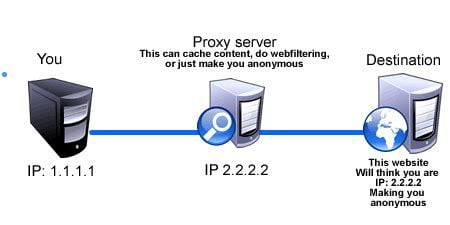
proxy
Mainly, there are three types of proxies –
- HTTP proxies
- SOCKS proxies
- Transparent proxies
As the name suggests, HTTP proxies are used to route HTTP traffic through the proxy server. HTTP proxies are best for anonymous web surfing or accessing blocked websites.
SOCKS proxies work for routing HTTP traffic and any other traffic generated from applications like video streaming, games, etc.
Transparent proxies, also called hidden proxies, are majorly used by employers to keep an eye on employees and restrict access to certain websites. Employees don’t even know their requests are getting through a proxy server.
As compared to VPN, proxies are slower. There are a ton of free proxies available on the internet, but most of them aren’t trustworthy and barely work.
Prons of Proxy
- Easy to use
- Best for accessing blocked websites faster
- Provide privacy if correct one is chosen
Cons of Proxy
- No traffic encryption
- Does not work at the Operating system level
- Slower than VPN
Tor Network
Tor network, aka. Onion network is the best method to protect online privacy so far. The reason it’s called onion network is that it has many layers of encryption. When a user sends a request through the tor network, the request goes through multiple devices on the network (3 devices). Each device receives the request, encrypts it, and forwards it to the next device in the row.
When the request reaches the last device, this device decrypts the request and sends it to the destination server. The destination server processes the request and sends the output back in the same manner. This way, the destination server never knows the real user’s identity.
We can configure the Tor network to route traffic from any application. To browse the internet privately through the Tor network, we do not need to configure anything. We can use Tor Browser. In the next article, I will show how to configure proxychains to take advantage of the Tor network in any application.
Tor Browser
Tor browser is a free and open-source web browser. Available for all major platforms, Tor Browser looks exactly like Firefox and Chrome, but it routes all the traffic through other devices on the network.
Download Tor Browser
Once downloaded, extract the files from the archive. Now run the binary file that says ‘start-tor-browser.desktop’. If you are on Windows, run the downloaded setup, and by default, tor browser will install on your Desktop.
For Linux users, move into the tor directory extracted from the downloaded archive and run ./start-tor-browser.desktop.
It’ll start the browser. Click “Connect” to connect to the tor network. Now you’re good to go. Visit any website as you would on any other browser. Additionally, you can also open .onion websites that are not accessible through browsers like Google Chrome or Firefox.
Prons of Tor browser
- Free & Open source
- Encrypts users traffice
- Almost impossible for Governments or anyone else to snoop into the tor network
- Journalists & activists can also use tor to share information with their sources
- Faster than proxies
Misconceptions about Tor Browser
Not many know about Tor Browser and even fewer who actually use it in their daily lives. Tor Browser is known to be a notorious web browser that opens up the “Dark Web”, only used for buying or selling drugs. Also, the size of this Dark web is a hundred times more than the surface web. All of it is not true.
Tor Browser provides a safer way to access the internet. It protects its users’ identities by encrypting and bouncing users’ traffic through different devices. Facebook, Wikipedia, and many other popular websites are also available as .onion so that users can browse these websites privately.
As with everything else, a few websites do sell drugs, but we can not call the entire network unsafe because of them. Bad actors are everywhere, including the normal Internet we use through Google chrome or Firefox.
